

Dynamic application security testing (DAST) is a form of security testing that involves the manual or automated testing of applications while they are in use. This type of security testing is used to identify vulnerabilities that could be exploited by attackers. DAST is often used in conjunction with static application security testing (SAST) to have a more comprehensive view of web application vulnerabilities.
Automated Penetration Testing is an evolutionary peer of DAST in the application protection sphere. On the other hand, DAST looks for vulnerabilities in applications that are being used. APT offers automated systems to identify and fix possible deficiencies. In combination, the integration of APT and SAST provides a complete perspective into the security of web applications and protects them from targeted attacks or exploitation of identified vulnerabilities.
There are many benefits of using DAST, including:
Dynamic Application Security Testing (DAST) and Static Code Analyzers (SAST) tooling are not always useful for red teamers since it can’t analyze all contemporary web application functions to provide a white-box view of web apps especially to realize authentication & authorization flaws.
With DAST evaluation, the process of integrating business logic conformance checks into authenticated scans and detecting access control breaches becomes more difficult.
Moreover, removing false positives is not simple, and finally, DAST scan in the SDLC after CI/CD process jeopardizes developer productivity and shift-left ideals.
Penetration testing as Code (PAC) provides significant benefits over using DAST tools. These benefits are summarized in the table below.
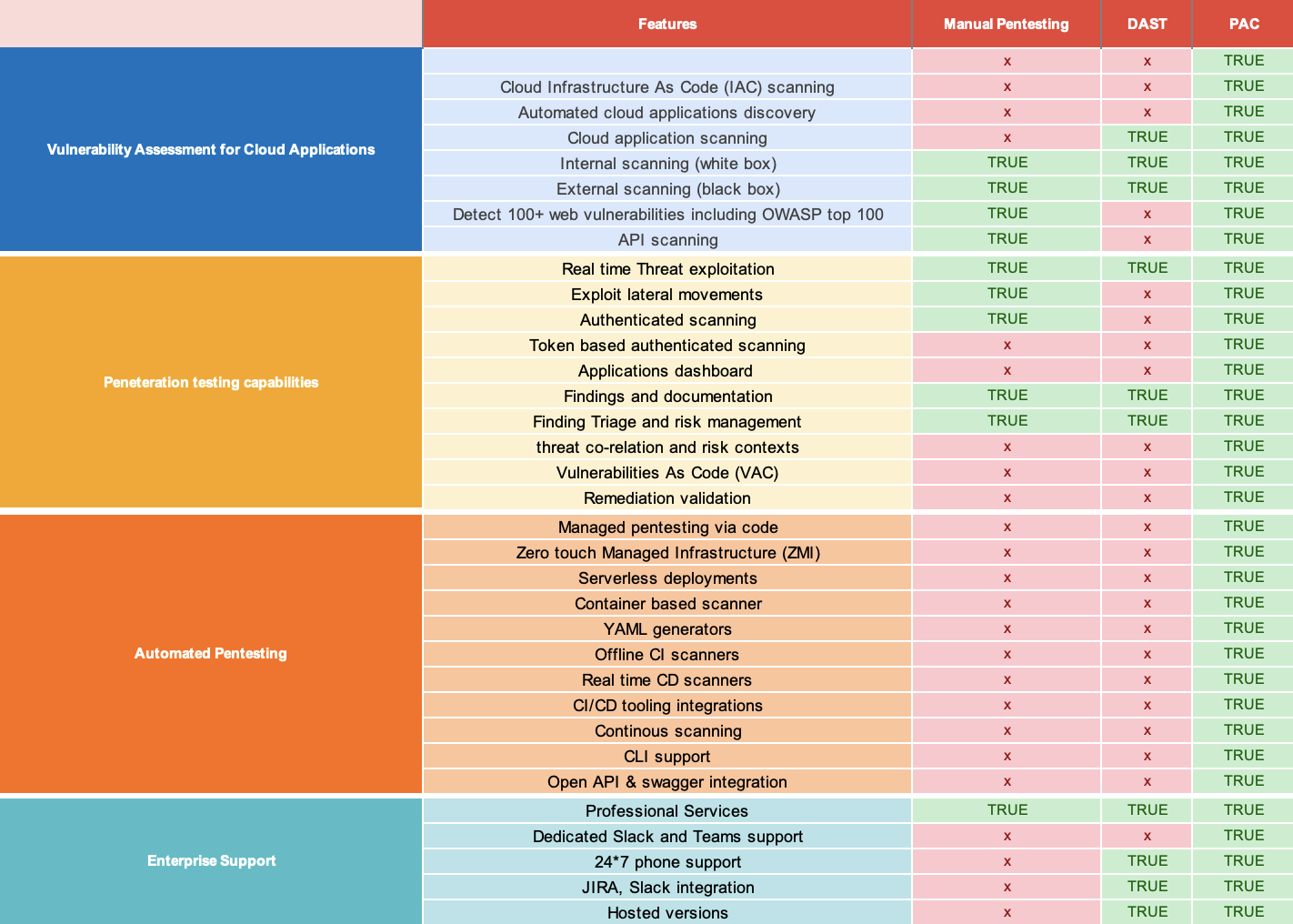
In Prancer, automatic security testing and real-time program safety checking (DAST) each have their own strong points and weaknesses when it comes to finding holes in computer systems’ software. DAST is more accurate because it connects directly with the target system. Meanwhile, automated penetration testing gives a wider view by trying to mimic real-world attacks. In the end, what you pick will be based on what your company needs and the kind of software being tested. No matter the method picked, constant and careful Automated hacking checking is vital for businesses. This helps them keep safe protection from possible online dangers.
