
Are you concerned about the increasing cyber threats to your organization? Do you want to secure your systems through penetration testing but find traditional approaches time-consuming, costly, and technically challenging?
Look no further! Prancer offers a revolutionary solution with its Automated Penetration Testing platform. Our platform combines low-code and no-code approaches to comprehensively cover your infrastructure, APIs, and web applications. It’s fast, user-friendly, and cost-effective – no coding or scripting experience is required! With Prancer’s fully automated Penetration Testing as a service (PTaaS) solution, you can swiftly and thoroughly penetration test your systems and identify vulnerabilities before malicious actors exploit them.
Don’t wait – sign up for a free trial today and experience the power of Prancer’s solution.

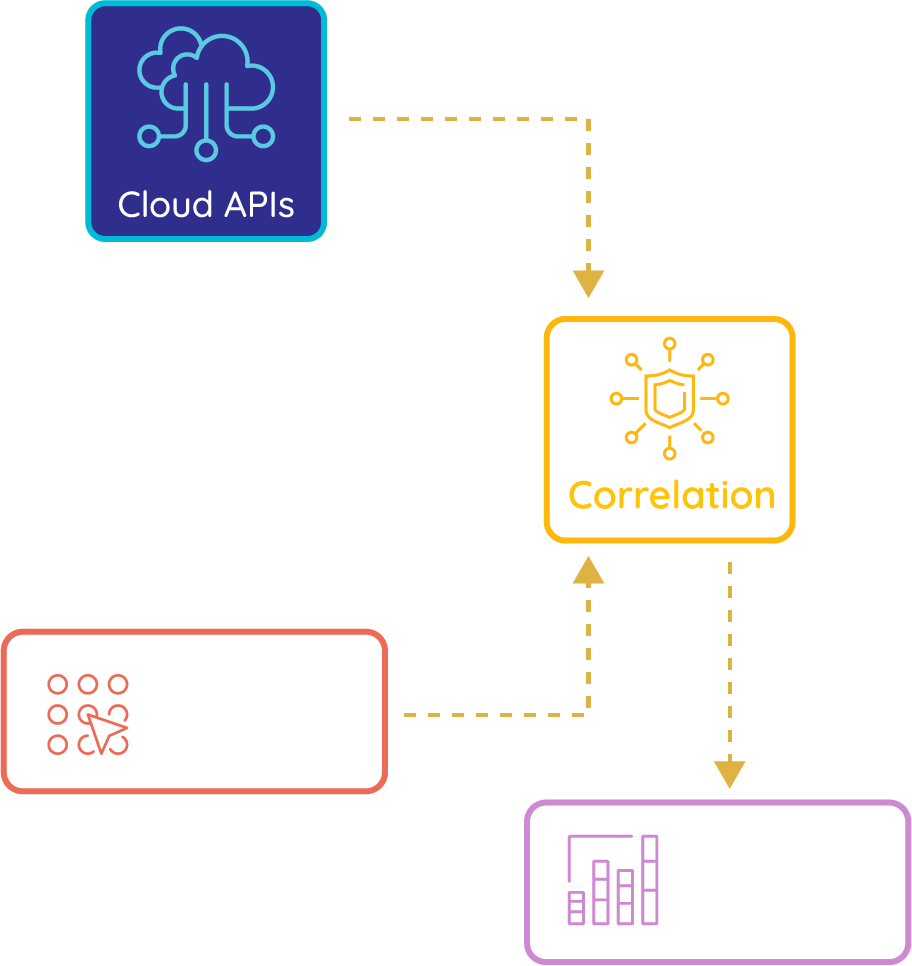
It's tedious for security experts to review a large number of findings from various security tools to understand the critical impact of attackers. Prancer's attack path analyzer evaluates the current risk score based on real-time application penetration testing findings and infrastructure vulnerability discoveries to provide a more accurate risk assessment. Protect your business with cyber security usecases and API security validation.
Prancer Enterprise, a leading innovator in cloud security solutions, is thrilled to announce the grant of a pivotal patent from the United States Patent and Trademark Office (USPTO) for its cutting-edge technology in automated penetration testing in cloud environments.


Siloed security tools and findings make it difficult to accurately view the overall risk posture. This can lead to a high number of false positives and inaccurate risk scores. Prancer's Automate Pentest As A Service (PTaaS) solution correlates and consolidates your infrastructure findings with application security findings to maximize the accuracy of risk scores.
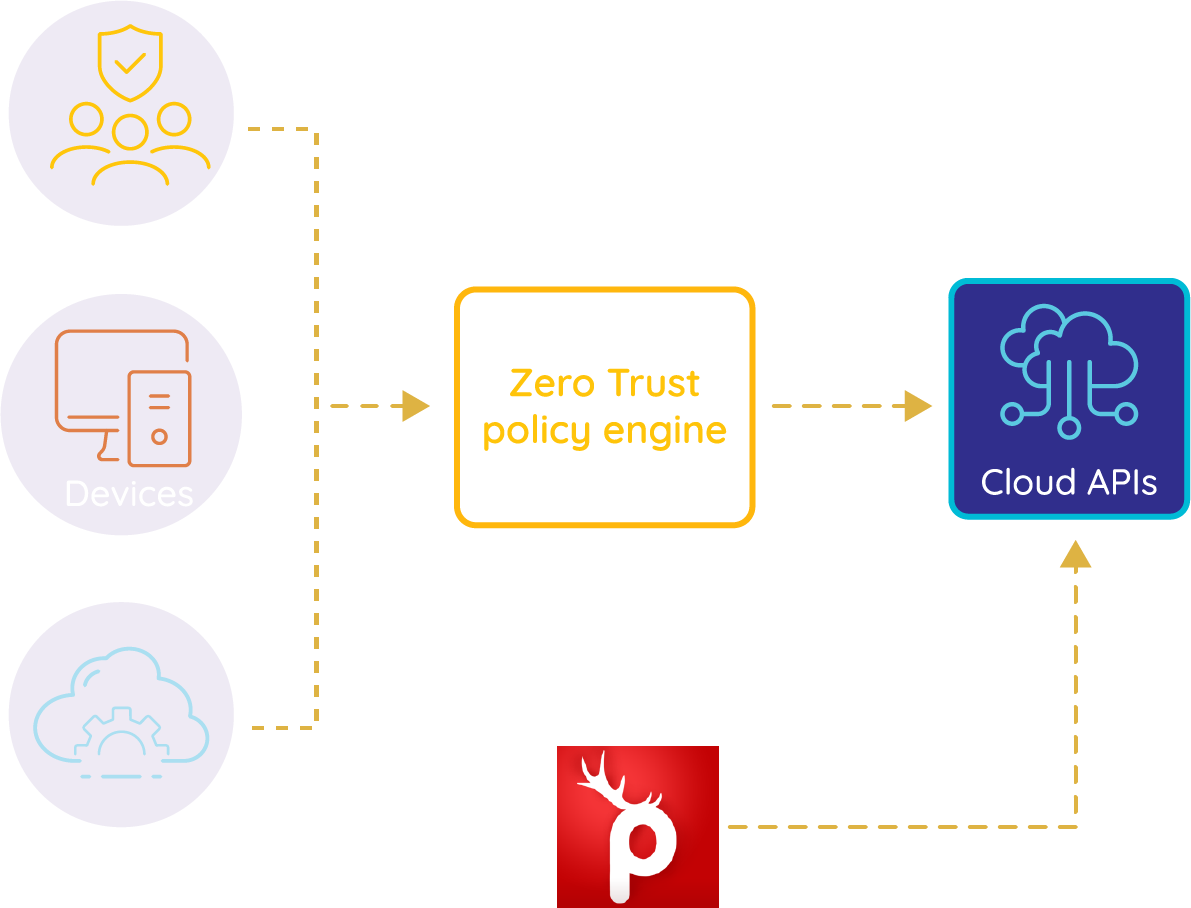
A zero trust approach fundamentally changes how applications are designed - now, they are meant to be internet-facing by default. Several tools exist to implement Zero Trust security, but one challenge is the automatic validation of policies at scale. Prancers PTaaS for Zero Trust Security Validation overcomes this hurdle by assuming different threat contexts at scale.


Prancer's fully automated Pentest As A Service (PTaaS) offers a unique combination of low- code and no-code approaches to provide unrivaled transparency and control to your infrastructure, APIs and Web Apps. Our Automated PTaaS platform makes it possible to automate the complex pentest use cases and scale them across multiple environments without hiring more pentesters.
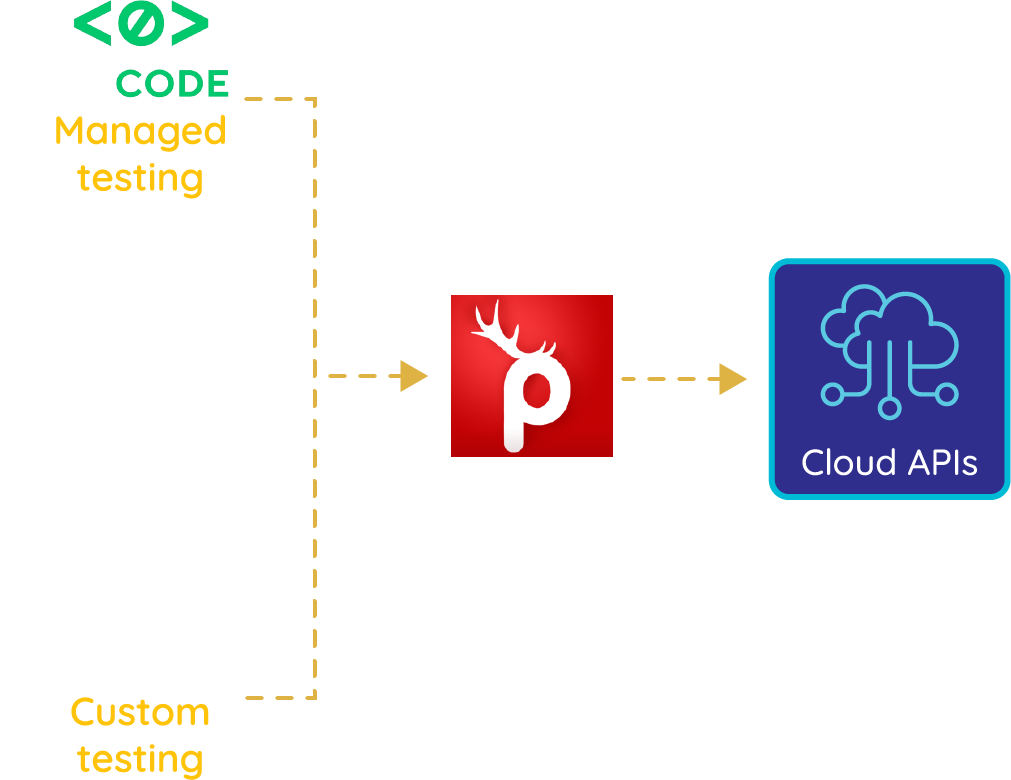
Offensive security testing should be handled earlier in the software development lifecycle as part of the developer experience because it can help developers build more secure code from the beginning. Prancer's fully automated PTaaS makes it possible to integrate security testing into the Continuous Integration/Continuous Delivery (CI/CD) process, which helps to shift left security testing and reduce its impact on the overall timeline.

San Diego, CA – May 24th 2023 – Prancer, a leading provider of cloud security solutions, is excited to announce the availability of its products on Azure Marketplace. This strategic move expands Prancer’s customer reach and provides existing clients with the convenience and acce...
Read moreThe cyber-world is constantly circling in tide pools of updates around application security, whic...
Read moreReinforcing the significance of the present generation, the cyber security domain has never been ...
Read more




