
In today’s digital landscape, ensuring robust cloud security is paramount for safeguarding applications and sensitive data. Automated security solutions play a crucial role in strengthening security, protecting against evolving threats, and mitigating risks. This article explores the importance and benefits of automated security, highlighting the value of Prancer’s advanced security solutions. Discover how Prancer can help you enhance your security, fortify your application security, and streamline your security processes.
The Role of Cloud Security: security encompasses a range of measures and practices aimed at safeguarding cloud-based applications and infrastructure. It involves protecting against unauthorized access, data breaches, malware, and other security threats. Automated security solutions provide continuous monitoring, rapid threat detection, and real-time response to enhance the security posture of your cloud environment.
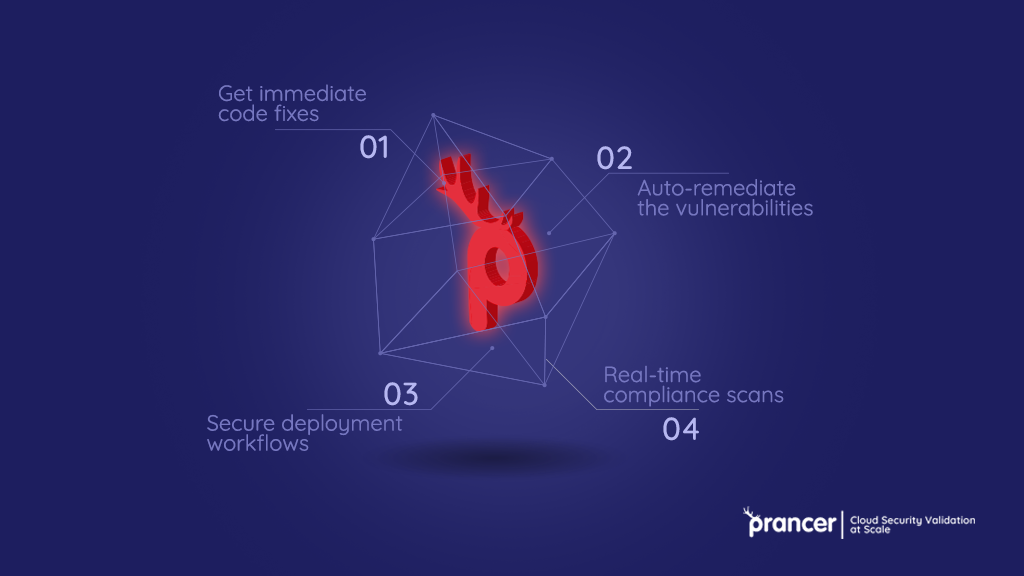
The Power of Automated Security: Prancer’s advanced automated security solutions offer a comprehensive suite of features to fortify your cloud security. By leveraging intelligent algorithms, machine learning, and real-time threat intelligence, these solutions provide proactive protection, continuous monitoring, and automated incident response, bolstering your application security in the cloud.
In addition to the automated security solutions highlighted above, Prancer offers features such as secure code storage, access controls, and real-time threat intelligence to further enhance security. With Prancer’s comprehensive suite of automated security solutions, you can streamline your security processes, protect sensitive data, and fortify your application security.
Fortify Your Application Security with Prancer’s Automated Security Solutions
Automated cloud security is essential for protecting your cloud-based applications and data from evolving threats. By leveraging Prancer’s advanced automated security solutions, you can enhance your security posture, detect and respond to threats in real-time, and ensure the integrity and availability of your applications. Safeguard your cloud environment, fortify your application security, and streamline your security processes with Prancer’s automated security solutions.