In the ever-evolving landscape of cybersecurity, the need for robust and comprehensive tools has never been more critical. Prancer’s PenSuite AI, a leading platform in the realm of attack emulation, stands out as a beacon of innovation and effectiveness. This blog post embarks on a journey to explore how Prancer has seamlessly integrated with the MITRE ATT&CK framework, enhancing security assessments and providing invaluable insights into potential vulnerabilities.
Exploring Prancer’s Interface: A Gateway to Enhanced Security Assessments
Prancer’s interface is meticulously designed to cater to the needs of security professionals, offering a plethora of features specifically tailored for attack emulation. Users can navigate through an intuitive dashboard, access various tools, and configure settings to suit their unique security requirements. This user-centric design ensures that even those with limited technical expertise can leverage Prancer’s capabilities to fortify their cybersecurity defenses.
Seamless Integration with MITRE ATT&CK Framework
At the core of Prancer’s functionality is its profound alignment with the MITRE ATT&CK framework, a globally recognized knowledge base of adversary tactics and techniques. By integrating with this framework, Prancer demonstrates its commitment to adhering to industry standards and providing users with a comprehensive view of potential security threats.
This integration allows Prancer to emulate a wide array of attack scenarios, providing users with actionable insights and recommendations for mitigating risks. Security teams can simulate real-world attacks, understand the potential impact on their systems, and take preemptive measures to bolster their defenses.
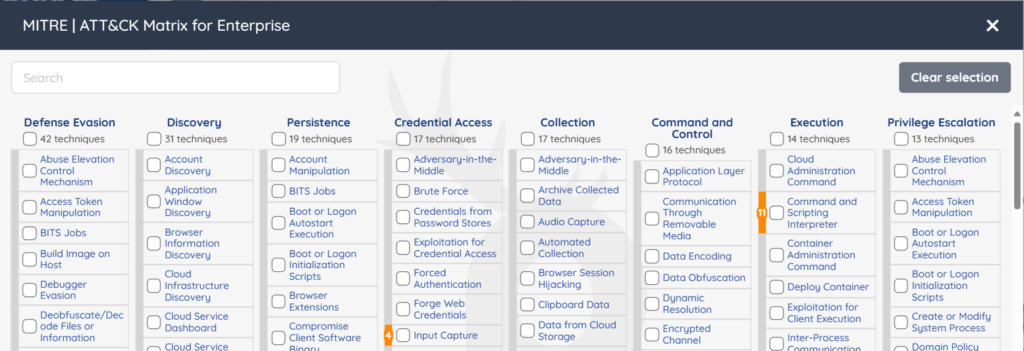
A Case Study with MITRE Attack Tactics:
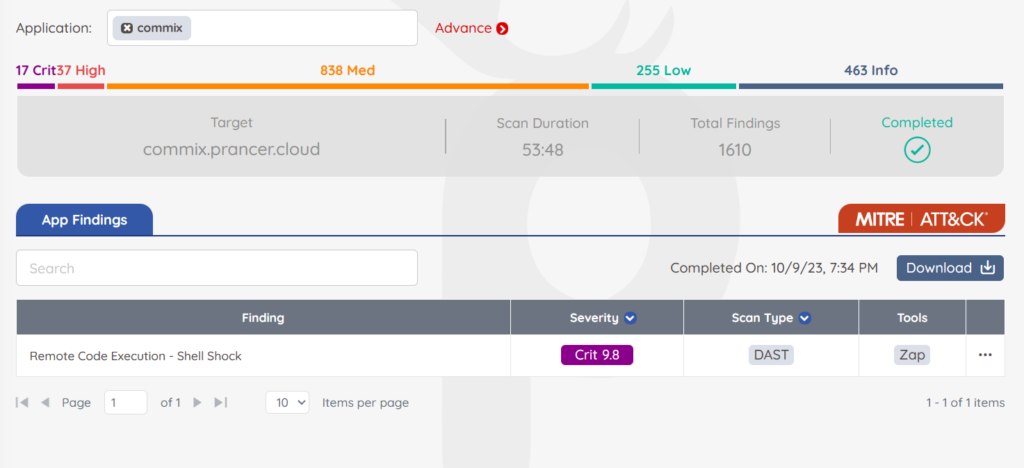
To illustrate the real-world impact of Prancer’s capabilities, let’s delve into a case study focusing on the exploitation of RCE Tactic, a prevalent vulnerability today.
The Vulnerability: RCE Tactic
In this scenario, an application is found to have a cookie misconfiguration issue, leading to RCE Tactic. Attackers exploiting this vulnerability can gain unauthorized access to user accounts and sensitive data.
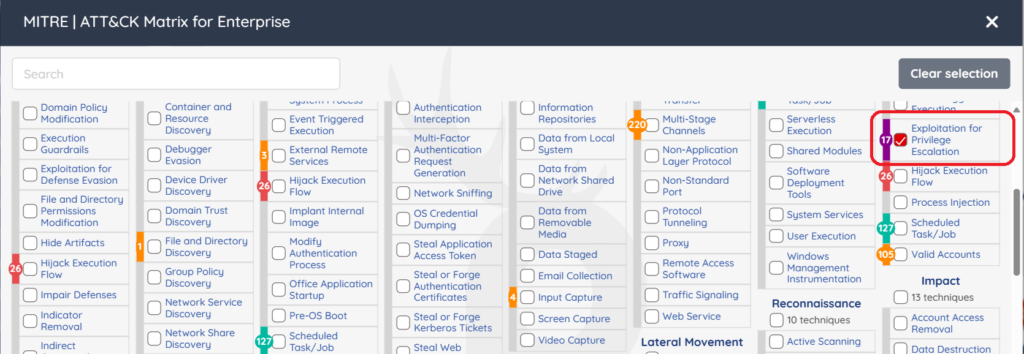
MITRE Attack Tactics
Utilizing Prancer’s attack emulation, the following MITRE ATT&CK tactics are employed to exploit the RCE Tactic vulnerability:
- Initial Access: Attackers gain access to the network by exploiting the cookie misconfiguration.
- Credential Access: Upon gaining initial access, attackers retrieve account credentials stored or transmitted insecurely.
- Lateral Movement: Using the compromised credentials, attackers move through the network, seeking additional access points and sensitive data.
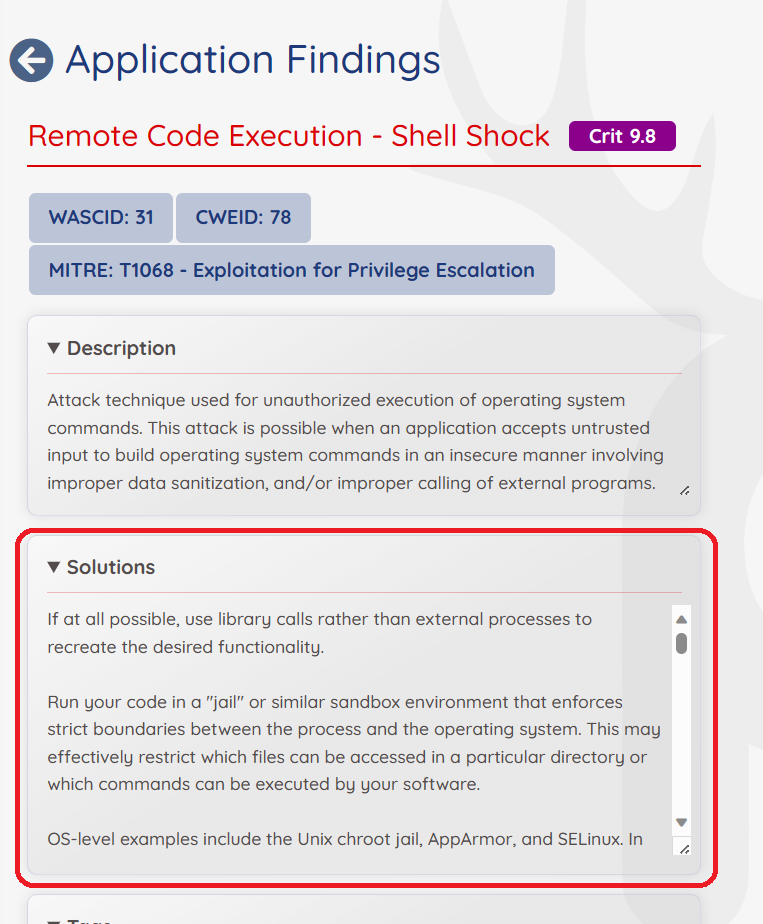
Mitigating the Risk
Prancer not only identifies and emulates these attack scenarios but also provides comprehensive mitigation strategies. In this case, security teams are guided to:
- Securely configure cookies and ensure that sensitive data is not stored or transmitted in an insecure manner.
- Implement robust encryption mechanisms for data in transit and at rest.
- Regularly monitor and audit access logs to detect any unauthorized access promptly.
Conclusion
Prancer’s journey to comprehensive attack emulation, underscored by its integration with the MITRE ATT&CK framework, marks a significant stride in the field of cybersecurity. By providing an intuitive interface, emulating real-world attack scenarios, and offering actionable mitigation strategies, Prancer empowers organizations to defend against a myriad of cyber threats proactively. Embrace the journey with Prancer, and fortify your cybersecurity defenses today.




