

as a DevOps engineer, I have to confess that I have checked in Infrastructure as Code (IaC) templates to the remote repo with secrets inside! (multiple times: – )
And this is not a pleasant experience. You have to start searching on stackoverflow how to change the git header, and then notify your manager about what happened, rotate the secrets… To rephrase that, lots of troubles!
Prancer Security platform can help you overcome this problem and have peace of mind for yourself and all other team members you are working with.
Prancer can prevent this problem by scanning every Infrastructure as Code (IaC) Template at each commit or when a PR is raised to ensure no secret is exposed in the Infrastructure as Code (IaC) template.
Secrets are usually in the form of passwords or other kinds of sensitive information inside the Infrastructure as Code (IaC) template. Here is an examples of Infrastructure as Code (IaC) templates with hardcoded secrets:
Terraform AWS:
resource “aws_db_instance” “default” {
allocated_storage = 10
engine = “mysql”
engine_version = “5.7”
instance_class = “db.t3.micro”
name = “mydb”
username = “foo”
password = “foobarbaz”
parameter_group_name = “default.mysql5.7”
skip_final_snapshot = true
}
Reviewing these Infrastructure as Code (IaC) templates and checking other public repositories on git providers for Infrastructure as Code (IaC), we understood four methods to find the secrets in Infrastructure as Code (IaC) code:
With Prancer secret scanner, we can search for specific keywords like “password”, “P@ssw0rd” “P@$$W0rd” or other combinations in the Infrastructure as Code (IaC) template.
Looking for patterns is being able to find some patterns inside the code to find the secrets. for example in case of Azure SQL in terraform, this is the code snippet you are assigning the password for the admin account:
resource “azurerm_sql_server” “example” {
name = “myexamplesqlserver”
resource_group_name = azurerm_resource_group.example.name
location = “West US”
version = “12.0”
administrator_login = “4dm1n157r470r”
administrator_login_password = “4-v3ry-53cr37-p455w0rd”
tags = {
environment = “production”
}
}
We can introduce the pattern to Prancer Secret Scanner and find it in all other Infrastructure as Code (IaC) templates.
With the entropy method, if there is a word with lots of numbers, upper case, lower case, or special characters, the entropy of that specific word is high. An error is raised, which mentions it could be a secret in the code.
Sensitive extensions are the ones who can have certificates, private keys, and other forms of sensitive information. Examples are *.CER or *.CRT – Base64-encoded or DER-encoded binary X.509 Certificate
Let us see how the Prancer platform finds secrets and passwords in Infrastructure as Code (IaC) templates.
We have vulnerable by design repositories on GitHub for each type of Infrastructure as Code (IaC) template Prancer supports. And intentionally, there are some secrets hard-coded into these repositories.
As an example, The AWS terraform files have some secret keys hardcoded inside the template. It is a security misconfiguration that has to be prevented.
https://github.com/prancer-io/prancer-terramerra/blob/master/aws/secret/main.tf
resource “alkira_credential_aws_vpc” “account1” {
name = “customer-aws-1”
aws_access_key = “ASIAIOSFODNN7EXAMPLE”
aws_secret_key = “wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY”
aws_account_id = “123456789012”
type = “ACCESS_KEY”
}
Another example there is an Azure SQL in the terraform, and an admin password is hardcoded inside the template, which is again a security misconfiguration. In this example, the secret is hardcoded inside the .tfvars file
https://github.com/prancer-io/prancer-terramerra/blob/master/azure/sql_servers/terraform.tfvars
location = “”
server_name = “prancer-sql-server2”
server_rg = “prancer-test-rg”
server_version = “12.0”
admin_user = “prancer_admin”
admin_password = “vijcykDaHarj+Oz5”
enable_ad_admin = false
sql_server_login = “sqladmin”
enable_sql_firewall = true
sql_fw_name = “prancer-sql-fw-block-200-net”
sql_fw_start_ip = “0.0.0.0/32”
sql_fw_end_ip = “10.254.200.255”
tags = {}
An example from the Google Cloud Platform, the terraform code in the tfvars file contains the password for the Kubernetes cluster.
https://github.com/prancer-io/prancer-terramerra/blob/master/gcp/container_cluster/terraform.tfvars
k8s_username = “”
k8s_password = “Root1234”
Apart from these terraform cases, the cloud-native formats are also supported; for example, another repository is called “prancer-armof” with hardcoded secrets. Inside the parameters file, there is a workspaceKey hardcoded inside the arm template.
https://github.com/prancer-io/prancer-armof/blob/f49ee2a7641ffe2076b93508ab50d7663469beae/VM/log_analytic_agent/vm.azuredeploy.parameters.json
How Prancer finds these secrets and reports them back to the DevOps engineer
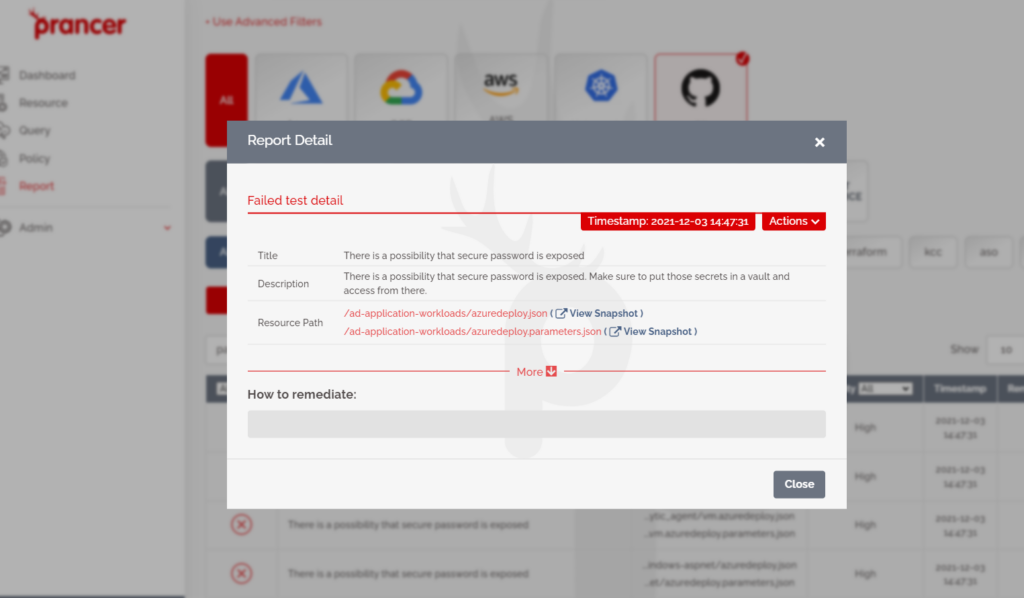
This is how Prancer finds the secrets and hardcoded passwords inside the IaC templates. This problem can be solved by moving the passwords to a secure vault the company uses.
