

In this blog post, we want to describe a new feature of Prancer Cloud Security Platform Static Code Analysis (SCA) engine for Infrastructure as Code (IaC). This blog post introduces a new feature that prevents sensitive files to be checked into git repositories.
Prancer Cloud Security Platform Static Code Analysis engine scans local and remote git repositories for all types of security misconfiguration. with this new feature, Prancer scanning engine analyzes the git repositories and if it finds any file with possible sensitive data in it, reports back to the DevOps engineers.
Sensitive information are usually in the following formats:
*.PFX or *.P12 – Personal Information Exchange Format
*.PEM – PEM or Privacy Enhanced Mail is a Base64 encoded DER certificate
*.CER or *.CRT – Base64-encoded or DER-encoded binary X.509 Certificate
*.CRL – Certificate Revocation List
*.CSR – Certificate Signing Request
*.DER – DER-encoded binary X.509 Certificate
*.P7B or *.P7R or *.SPC – Cryptographic Message Syntax Standard
.Key – key files
Prancer Static Code Analysis engine scans the repository for sensitive files.
Based on this list of possibly sensitive data, Prancer Static Code Analysis engine provides a report with all files that could contain sensitive information. This is very important when committing these files to repositories due to the risk of leakage of confidential data. On the report page for IaC scans, you can see the result of finding these sensitive data:
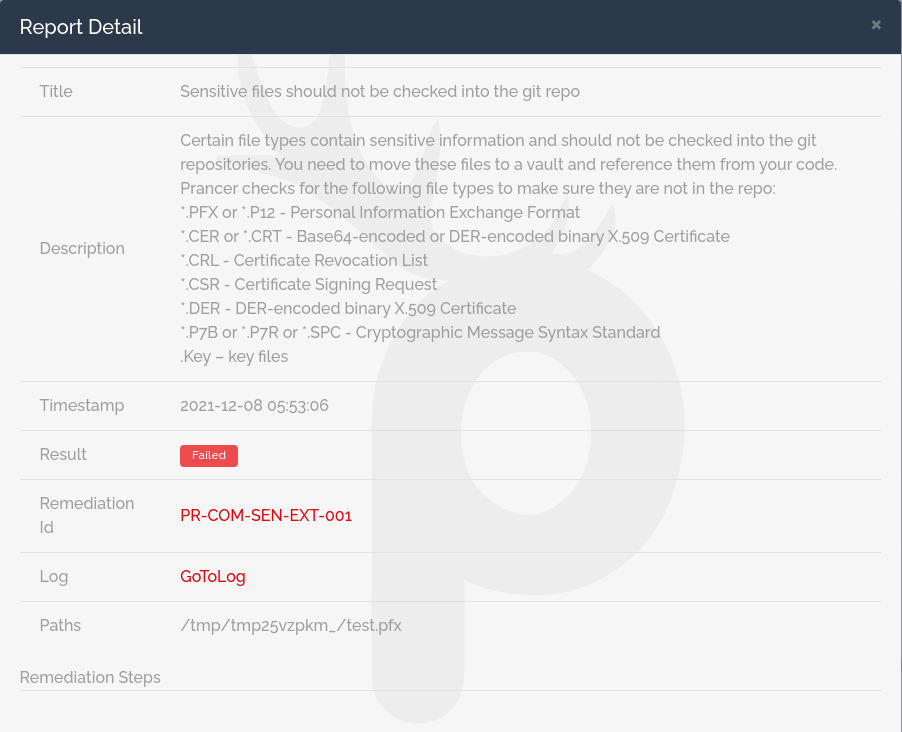
Noncompliance title: Sensitive files should not be checked into the git repo
Noncompliance description: Certain file types contain sensitive information and should not be checked into the git repositories. You need to move these files to a vault and reference them from your code. Prancer checks for the following file types to make sure they are not in the repo:
*.PFX or *.P12 – Personal Information Exchange Format
*.CER or *.CRT – Base64-encoded or DER-encoded binary X.509 Certificate
*.PEM – PEM or Privacy Enhanced Mail is a Base64 encoded DER certificate
*.CRL – Certificate Revocation List
*.CSR – Certificate Signing Request
*.DER – DER-encoded binary X.509 Certificate
*.P7B or *.P7R or *.SPC – Cryptographic Message Syntax Standard
. Key – key files
How to remediate
you need to add these extensions to your .gitignore file to prevent them from checking in to your repository. these files need to be moved securely to a vault to be managed securely and then referenced in your code.
Conclusion
In this blog post, we introduced a new Static Code Analysis engine feature that prevents sensitive files to be checked into git repositories. The latest version of the Prancer Static Code Analysis scanning engine for IaC scans can prevent sensitive data in your code to be checked into the git repositories that will reduce the risk of leakage while increasing the security of your IaC pipeline.