
How safe are your Kubernetes cloud resource configs in your Git repos? The one you forked from open-source projects? Prancer KCC reporting can quickly tell you just how secure or not it is.
As enterprise cloud platform teams are rapidly adopting Kubernetes to be a single pane of glass solution to deploy both cloud infrastructure and applications, major CSPs have open-sourced k8s cloud resource definitions such as KCC (Google’s k8s config connect), ASO (Azure Service Operator), ACK ( AWS controller for K8s) that manages cloud resources as Kubernetes resources. This enables a single consistent place to provision and configures your entire application without switching between multiple tools and conventions.
Prancer Enterprise, an Industry leader in static code analysis for IAC, recently released several new features to evolve as the first security vendor to provide automated static code analysis for K8s cloud resource definitions for GCP, AWS, and Azure.
As a continuous effort to safeguard our customers from supply chain risks associated with untrusted IAC, Prancer releases new open-source reporting for official Kubernetes cloud resource config projects. Prancer’s crawler engine continuously scans the opensource repos of the CSPs, validates against its OPA-based policy engine, and publishes the findings as scan reports.
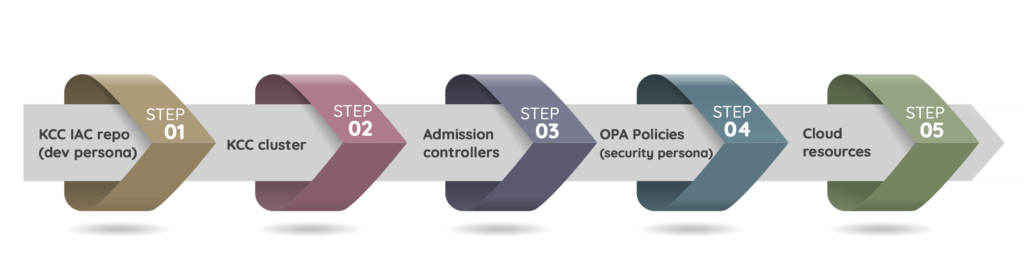
Traditionally k8s admission controllers utilize OPA-based gatekeeper policies to inspect the security configurations of the k8s deployment files. However, a critical problem space for platform security teams is the operational difficulties with running the admission controllers in the Kubernetes clusters that govern the deployments, the latency it introduces at the deployment time, and maintaining the gatekeeper policies up to date.
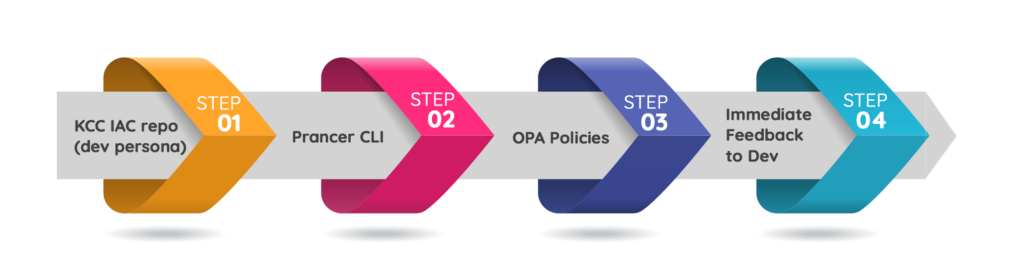
Prancer Enterprise untangles these challenges by enabling offline scanning on the project repos with no connectivity to k8s clusters. With Prancer CLI integration to CI /CD, the deployment files are scanned on each commit or pull request to provide actionable feedback to the developers on IAC configurations, thus shifting security to the left.
The scan reports are available at Prancer’s opensource repo here, and the top risk findings include lack of encryption, insecure firewall policies, lack of logging, etc.
