

You can integrate prancer Platform into your DevOps process to do automated security tests on Infrastructure as Code (IaC). This post will explain how to do an IaC security scan with Prancer platform on your Azure ARM templates repository in a few steps.
Hello World repositoryconnector fileHello World repositorygit clone https://github.com/prancer-io/prancer-hello-world.git
cd prancer-hello-worldTo clone the Prancer Hello World repository and change the directory to it.
You should modify the Connector file to point to your own git repository. The sample connector file is gitConnectorArm.json.
vi gitConnectorArm.jsonYou see the content of the file as follows:
{
"fileType": "structure",
"type": "filesystem",
"companyName": "prancer",
"gitProvider": "https://github.com/prancer-io/prancer-armof.git",
"branchName": "master",
"private": false
}Change the gitProvider to point to your repository. You can find more information about the structure of this file here
First, crawl your repo and then run the tests with the following commands.
prancer scenario-arm-remote --crawler
prancer scenario-arm-remoteYou will see the results of the tests on screen.
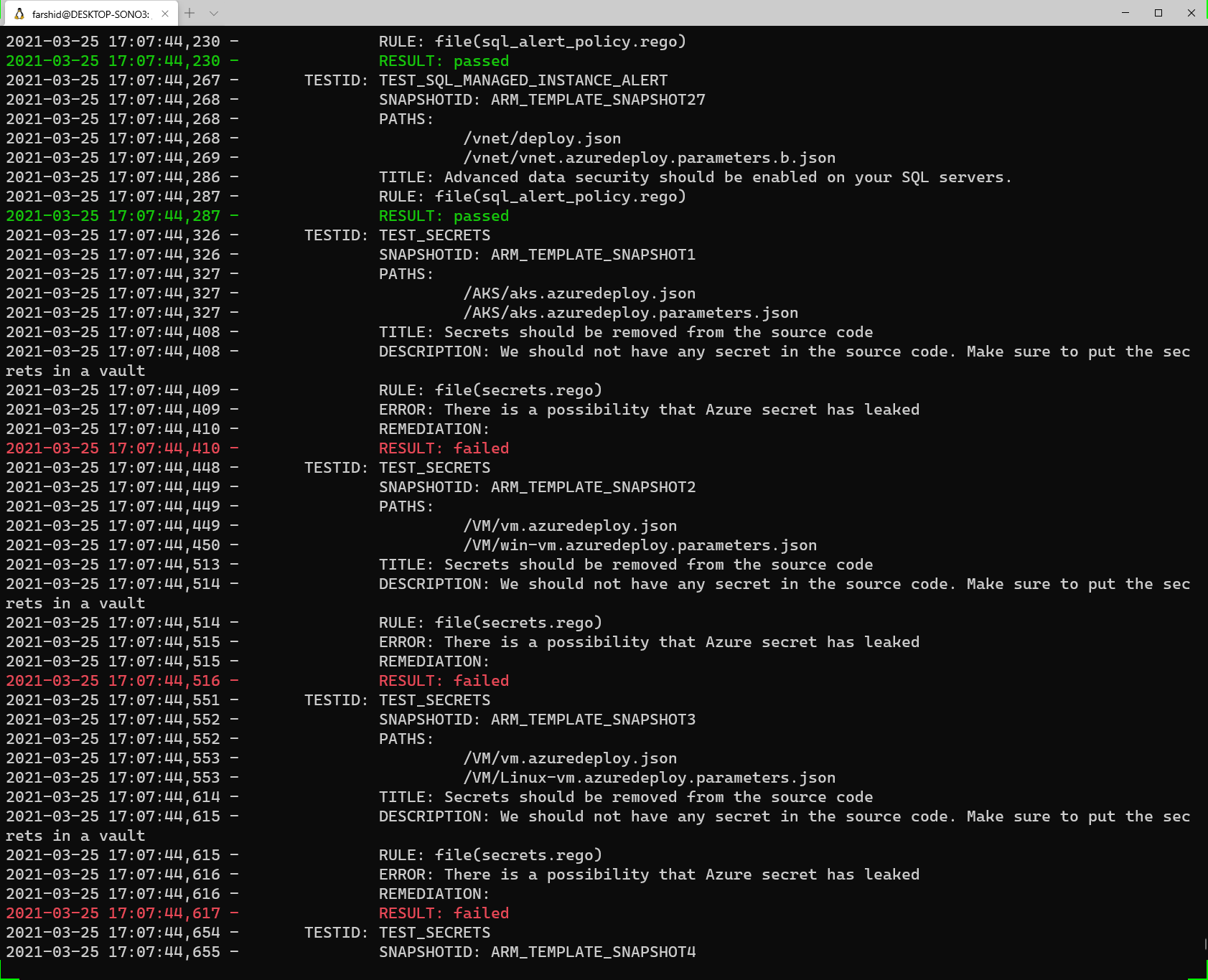
Prancer will generate an output file, and you can view the result of each test (Passed / Failed)
cat validation/scenario-arm-remote/output-master-test.jsonHere is a snippet of the output-master-test.json file:
{
"eval": "data.rule.aks_cni_net",
"result": "passed",
"message": "",
"id": "PR-AZR-0006-ARM",
"remediation_description": "Make sure you are following the ARM template guidelines for AKS from this URL : https://docs.microsoft.com/en-us/azure/templates/microsoft.containerservice/managedclusters",
"remediation_function": "PR_AZR_0006_ARM.py",
"snapshots": [
{
"id": "ARM_TEMPLATE_SNAPSHOT1",
"structure": "filesystem",
"reference": "master",
"source": "gitConnectorArmRemoteStructure",
"collection": "armtemplate",
"type": "arm",
"region": "",
"paths": [
"/AKS/aks.azuredeploy.json",
"/AKS/aks.azuredeploy.parameters.json"
]
}
],
"autoRemediate": false,
"masterTestId": "TEST_AKS_1",
"masterSnapshotId": [
"ARM_TEMPLATE_SNAPSHOT"
],
"type": "rego",
"rule": "file(aks.rego)",
"title": "Azure CNI networking should be enabled in Azure AKS cluster",
"description": "Azure CNI provides the following features over kubenet networking:_x000D__x000D_- Every pod in the cluster is assigned an IP address in the virtual network. The pods can directly communicate with other pods in the cluster, and other nodes in the virtual network._x000D_- Pods in a subnet that have service endpoints enabled can securely connect to Azure services, such as Azure Storage and SQL DB._x000D_- You can create user-defined routes (UDR) to route traffic from pods to a Network Virtual Appliance._x000D_- Support for Network Policies securing communication between pods._x000D__x000D_This policy checks your AKS cluster for the Azure CNI network plugin and generates an alert if not found.",
"tags": [
{
"cloud": "git",
"compliance": [],
"service": [
"microsoft.containerservice"
]
}
],
"snapshotId": [
"ARM_TEMPLATE_SNAPSHOT1"
],
"status": "enable"
}It provides you all the details you need to track down the item and fix it if required.
You can easily integrate the Prancer Platform into your pipeline for automated IaC scans.
fail_success=`grep failed validation/scenario-arm-remote/output-master-test.json`
pass_error=`grep passed validation/scenario-arm-remote/output-master-test.json`
if [[ -z "$fail_success" ]] || [[ ! -z "$pass_error" ]] ; then echo "scenario-arm-remote failed"; exit 1;fi